top of page


We create blogs that delve into various Microsoft technologies such as Intune, Azure AD, Defender, Azure, and Endpoint Security. Our articles highlight the solutions and challenges we in our everyday work.
Search

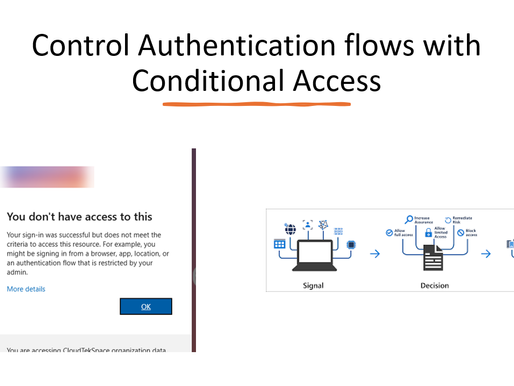



bottom of page


We create blogs that delve into various Microsoft technologies such as Intune, Azure AD, Defender, Azure, and Endpoint Security. Our articles highlight the solutions and challenges we in our everyday work.





